select the best answer. which of the following are breach prevention best practices
Which Of The Following Are Breach Prevention Best Practices - Fit Food Fashion. Best practices for breach prevent are.

Top 15 Network Security Websites
Access only the minimum.

. Logoff or lock your workstation when it is unattended. 12 charts show the. In this type of data breach a.
Implementing encryption standards and backup policies to decrease risks and make sure that software is up. Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. Quality assurance QA is a crucial aspect of breach prevention.
Set up two-factor authentication for every account. Under the Privacy Act individuals have the right to request amendments of their records contained in a system of records. Which of the following are breach prevention best practicesAccess only the minimum amount of.
Which of the following are breach prevention best practices. Research shows that around 30 of ROI authorizations are initially invalid and without QA checks. And privacy officials select reasonable and appropriate.
Administrative actions and policies and procedures that are used to manage the selection development implementation and maintenance of security measures to protect electronic PHI. 30 Best Practices for Preventing a Data Breach. Which of the following are breach prevention best practices.
Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the. All of this above Best practices for breach prevent are. D communicating a purchase order to a supplier.
7 Key Steps To Investigate A Data Breach With Checklist Ekran System Data Breach Response Times Trends And Tips Mitigating Insider Threats Plan Your Actions In. Data Breach by an Insider. Which of the following are breach prevention best practices.
30 Best Practices for Preventing a Data Breach. Which of the following are breach prevention best practices. However before jumping to Breach Prevention Best Practices lets get to know frequently observed Data Breach types.
All of the above. Which of the following are breach prevention best practices. Which of the following are breach prevention best practices.
Two-factor authentication is a security feature that requires. Select The Best Answer. Misdirected communication containing PHI or PIIC.
Identify areas that store transmit collect or process. Promptly retrieve documents containing PHIPHI from the. Access only the minimum amount of phipersonally identifiable information pii necessary.
Promptly retrieve documents containing PHIPHI from the printer. Identity sensitive data collected stored transmitted or processes. A Privacy Impact Assessment PIA is an.

Top Five Best Practices For Preventing Phishing Attacks
21 Server Security Tips Best Practices To Secure Your Server Quickly

Breach Prevention 5 Best Practices To Protect Your Data Mro Corp

11 Ways To Prevent Data Loss And Data Breaches In 2022 Easydmarc

Data Loss Prevention Next Steps
![]()
How To Quantify The Cost Of A Data Breach A Case Study
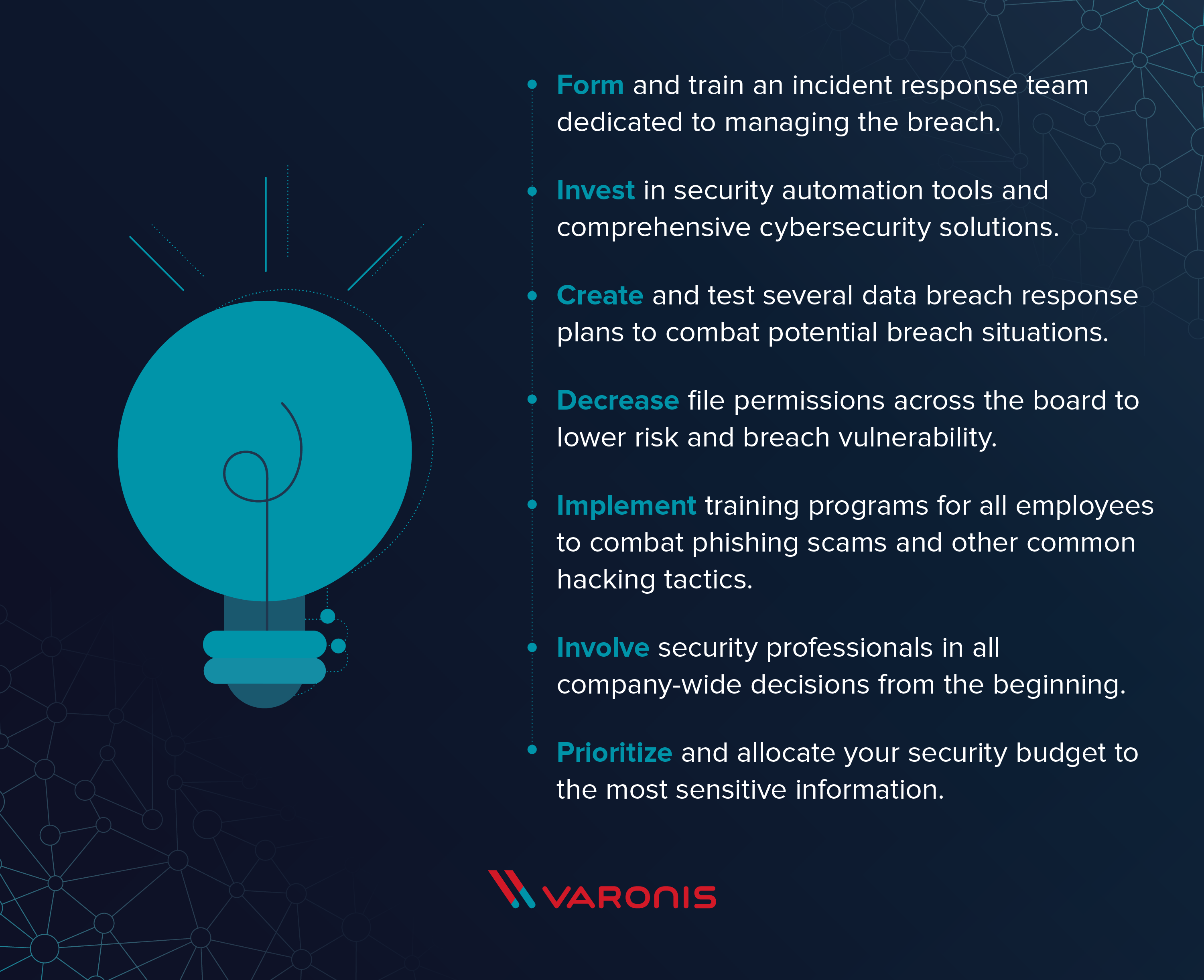
Data Breach Response Times Trends And Tips

A Principals Guide To Promoting Digital Citizenship And Student Data Security Powerschool

10 Biggest Data Breaches In Finance Updated August 2022 Upguard

How To Apply Incident Response For Saas Polymer

5 Ways Big Companies Protect Their Data Endpoint Protector

Software Data Breach Overview Veracode
4 Security Measures Companies Implement After A Breach

12 Types Of Malware Examples That You Should Know
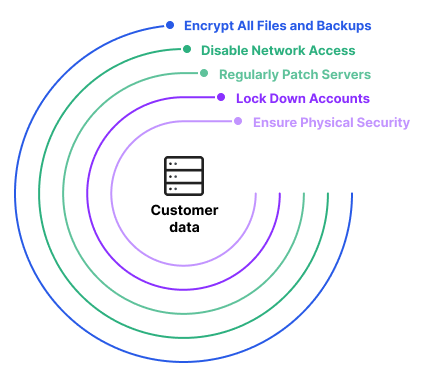
What Is Database Security Threats Best Practices Imperva

Microsoft Sentinel Critical Start

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero